CI/CD Security vs. Security-as-Code: which lowers risk more?
Vulnerability injections in the CI/CD pipeline recently led to open source projects making headlines. Here’s a better way to secure.
Learn more
Protect both modern and legacy applications & APIs with the only platform that not only stops exploits but also corrects the vulnerable code, eliminating exploitability.
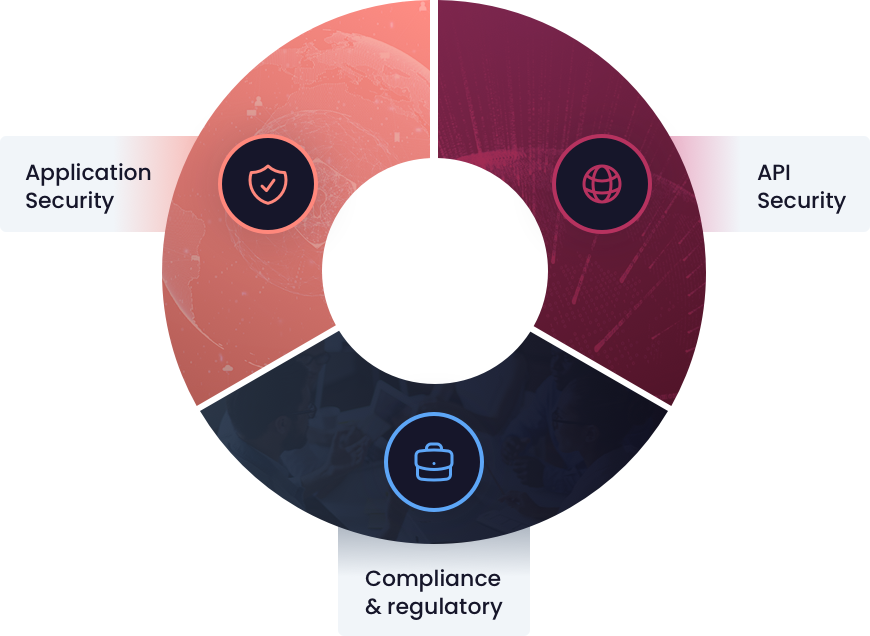





Only Waratek combines Java software and security engineering expertise, to automate the manual process of fixing code vulnerabilities. This unique combination provides turnkey protection against generic and JVM-specific vulnerabilities.
Signature-based security platforms scrutinize HTTP request payloads for pattern matches, assuming risk. However, this time-consuming and costly process is impractical for each request, let alone every application and API.
Waratek operates within your applications' runtime, tracing how network data flows through the application or API. When data misuse occurs, Waratek corrects the vulnerable code, effectively neutralizing the threat posed by untrusted data almost instantly with little performance overhead.
By tracing data flow through the application or API, we can identify when untrusted network data interacts with vulnerable code. When such interaction occurs, Waratek's Java Security Platform instantly replaces the vulnerable code in memory with a remediated version.
This real-time swap ensures future references to the code will use the remediated version, guaranteeing every request—not just one out of a thousand—is thoroughly protected as there's no vulnerability to exploit anymore.
Waratek's Java Security Platform not only found the cryptominer we had, but securely removed it within 48 hours, stopping us from having to rebuild our solution from scratch.
Waratek Secure delivers speed, accuracy, and resilience in Java applications & APIs. Swiftly identify and precisely resolve vulnerabilities in real-time, ensuring your systems remain resilient against ever-evolving cyber threats.
Learn moreWaratek Elevate ensures legacy constraints don't compromise your security. Virtually upgrade your apps and APIs to meet compliance like TLS 1.2 and eliminate EOL version vulnerabilities.
Learn more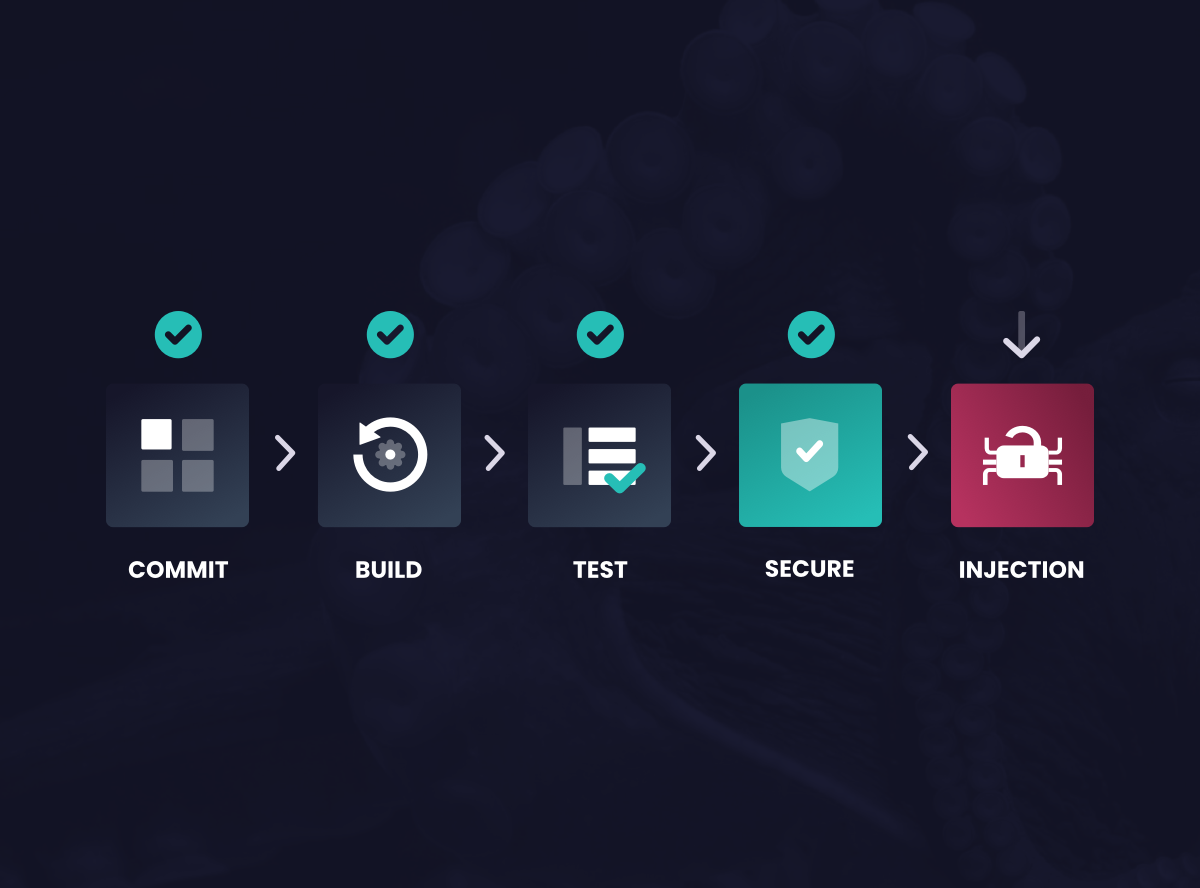
Vulnerability injections in the CI/CD pipeline recently led to open source projects making headlines. Here’s a better way to secure.
Learn moreWork with us to accelerate your adoption of Security-as-Code to deliver application security at scale.