CI/CD Security vs. Security-as-Code: which lowers risk more?
Vulnerability injections in the CI/CD pipeline recently led to open source projects making headlines. Here’s a better way to secure.
Learn more
Bolster your legacy applications' security profiles, fortifying them against modern threats, and aligning them with today's stringent security requirements.
Waratek Elevate ensures legacy constraints don't compromise your security. Virtually upgrade your apps and APIs to meet compliance like TLS 1.2 and eliminate EOL version vulnerabilities.
Waratek's Java Security Platform not only found the cryptominer we had, but securely removed it within 48 hours, stopping us from having to rebuild our solution from scratch.
More than 74% of enterprises are aggressively starting legacy modernization projects to adopt modern cloud platforms.
Waratek Elevate wraps your legacy applications in a modern version of JRE, helping you instantly take advantage of the security and regulatory benefits of a modern tech stack without code changes.
Reap the benefits of modern cloud platforms without replacing thousands of applications.
Elevate allows security teams to package legacy applications in a portable, infrastructure-agnostic container.
This portability enables you to take advantage of modern infrastructure innovations while meeting security and regulatory requirements.
Can't find the answer you’re looking for? Reach out to our sales team.
The TLS-Upgrade rule allows Java applications to benefit from the latest and more secure TLS protocols and cipher suites without requiring any code modifications. This rule operates by transparently replacing outdated cryptographic protocols with the latest and trusted ones, mitigating common vulnerabilities.
Waratek Secure's Secure Sockets rule transforms plain TCP server sockets into SSL/TLS server sockets, creating a secure, encrypted communication channel. This rule operates transparently and addresses known vulnerabilities like CWE-319, CWE-311, and CWE-5, classified under "Sensitive Data Exposure" in OWASP's Top 10 list.
No, one of the key benefits of Waratek Elevate is that it offers significant security improvements without the need for code modifications. This means you can improve your applications' security profiles and align them with current standards without any disruptions to your operations.
How does it work?
Waratek Elevate wraps the entire application stack, including the original JRE in a guest container running as a servlet on the host machine.
The host machine maintains an up-to-date version of JRE that the client machine then communicates with securely with either ultra-low performance impact or, in specific scenarios, a performance increase.
How performant is this solution?
Performance is normally a difficult subject when it comes to legacy application modernization.
Waratek Elevate is the only legacy modernization solution that's been known to increase performance without code changes.
In other scenarios where performance cannot be increased, the overhead is less than 2% in production.
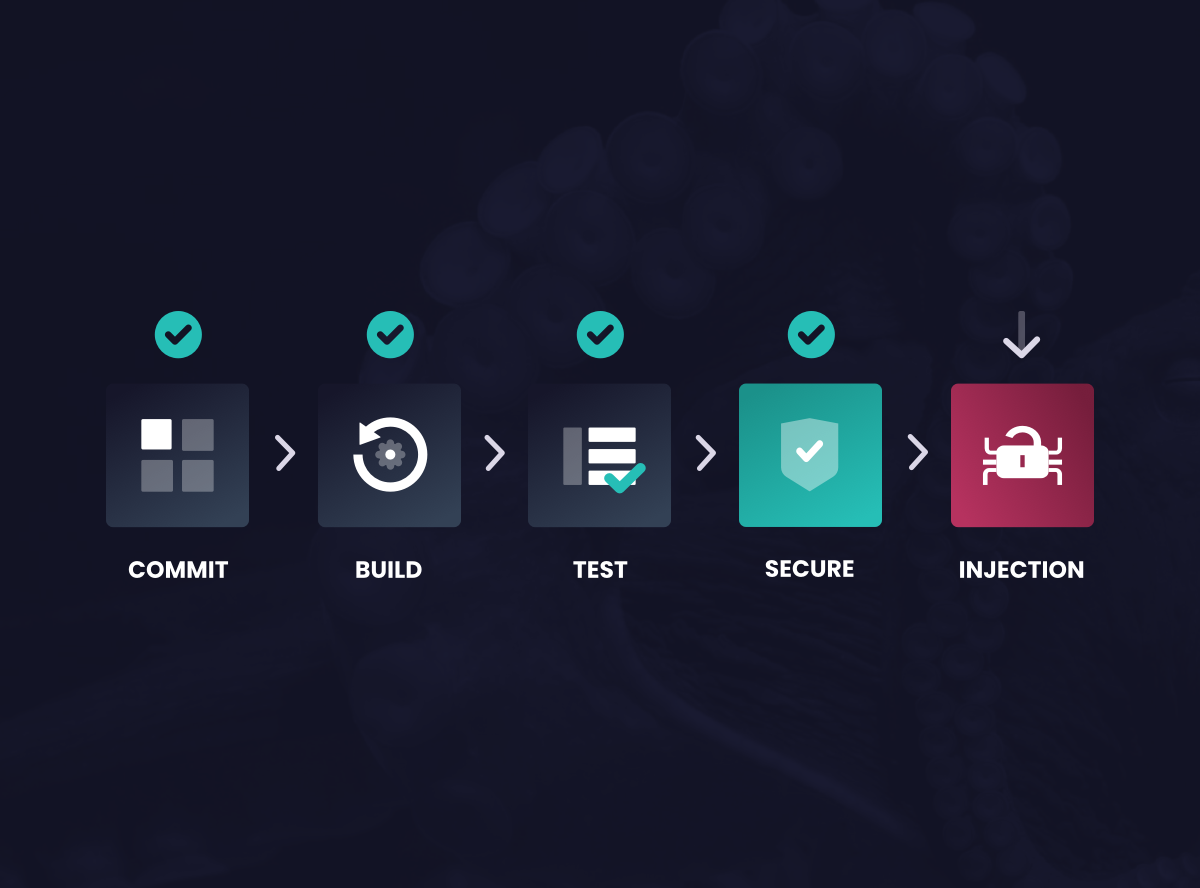
Vulnerability injections in the CI/CD pipeline recently led to open source projects making headlines. Here’s a better way to secure.
Learn moreWork with us to accelerate your adoption of Security-as-Code to deliver application security at scale.