Scale security to every application
Signature-based security platforms scrutinize HTTP request payloads for pattern matches, assuming risk. However, this time-consuming and costly process is impractical for each request, let alone every application and API.
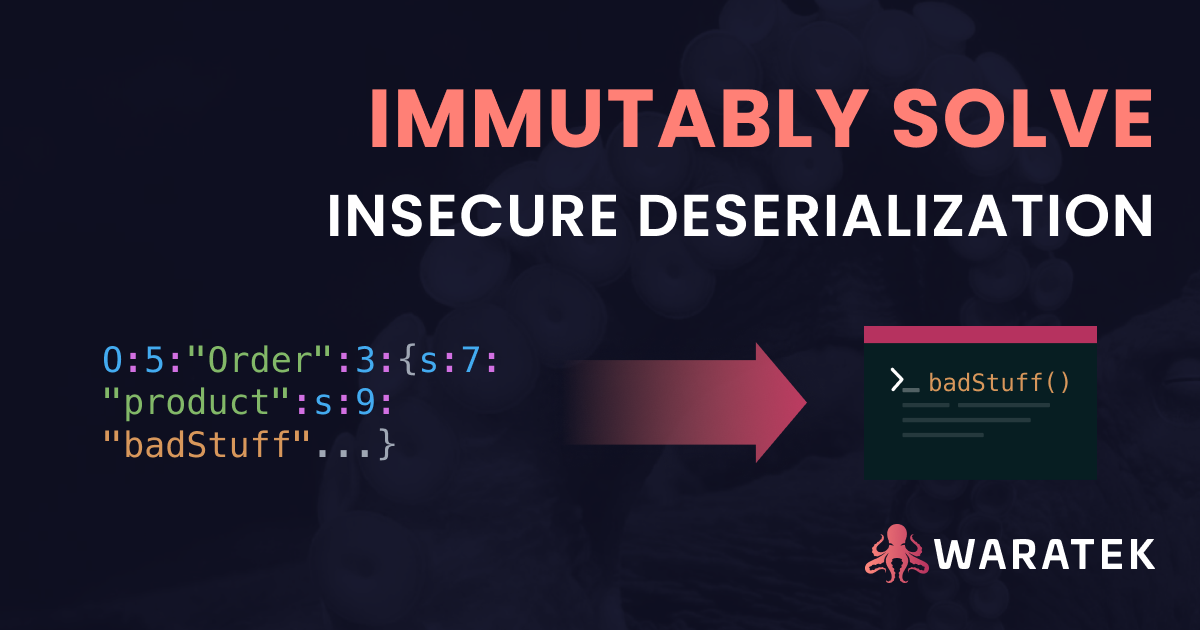
Waratek operates within your applications' runtime, tracing how network data flows through the application or API. When data misuse occurs, Waratek corrects the vulnerable code, effectively neutralizing the threat posed by untrusted data almost instantly with little performance overhead.
Stop every exploit every time
By tracing data flow through the application or API, we can identify when untrusted network data interacts with vulnerable code. When such interaction occurs, Waratek's Java Security Platform instantly replaces the vulnerable code in memory with a remediated version.
This real-time swap ensures future references to the code will use the remediated version, guaranteeing every request—not just one out of a thousand—is thoroughly protected as there's no vulnerability to exploit anymore.