Enterprise Resource Planning (ERP) systems are an invaluable asset to modern businesses. They assist in business operations, consolidate costs and functions, and provide critical insights that help companies do business more efficiently. They are also customizable to each organization’s needs, providing modules for finance, human resources, supply chain, and customer relationship management, all in a unified system.
However, the very features that make ERP systems so useful also make them prime targets for cyber attacks. This is particularly concerning because ERP systems often house a company’s most sensitive data — including financial records, intellectual property, and personal employee information.
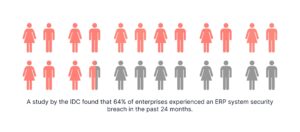
The interconnectedness of ERP systems both creates entry points for attackers to gain footholds and allows them to easily move laterally amongst different modules. A vulnerability in one module can potentially expose other modules to attack.
For example, in 2023, attackers exploited a SQL injection vulnerability in the MOVEit file transfer software, which allowed them to gain access to the system. Once inside, they could move laterally across interconnected ERP modules, accessing sensitive data and escalating their privileges. Attackers deployed webshells and malicious scripts, which facilitated their movement and enabled them to compromise additional modules like financial management, supply chain management, and human resources.
Hardening ERP Systems
Much of the risk associated with ERP systems can be reasonably mitigated by implementing diligent security practices. Steps like employing network segmentation and multi-factor authentication can meaningfully move the needle on reducing risk. Meanwhile, continuous monitoring helps detect and snuff out unauthorized lateral movement within ERP systems. However, these measures can take a lot of resources to maintain and any slip up in vigilance (like those which may happen during holidays or high-traffic events) will open up avenues for attack.
Traditional security measures, such as firewalls and intrusion detection systems, operate at the network level and are often limited by their inability to understand the context of application-specific threats. This means they also have to operate around the application, focusing on perimeter defenses. They present an obstacle for attackers attempting to gain initial access, but once one has snuck through, they can escalate privileges without much fear of interference.
RASP in ERP Security
To optimize your ERP security program to avoid those downsides and keep your modules insulated, implementing a Runtime Application Self-Protection (RASP) solution is a great option. RASP operates far deeper into the application and its functions than most security solutions do, which makes it uniquely positioned to protect the sensitive financial, HR, and supply chain data flowing through ERP systems. This technology embeds security policies and monitoring directly into the runtime environment of applications, enabling them to detect and mitigate threats in real-time.
Where other measures focus on perimeter defense, RASP provides continuous protection against internal lateral movement — to which ERP is most susceptible. It can provide insights into the application’s internal workings and its interactions with the runtime environment. This enables RASP to detect sophisticated attacks that may bypass perimeter defenses, such as SQL injection and cross-site scripting (XSS). It does this by continuously monitoring the application’s behavior to determine the patterns of normal operations and responds to anomalies in real-time.
All this means that RASP provides a more granular and dynamic defense mechanism than other methods. Moreover, RASP automates the response to security incidents, reducing the burden on IT and security teams and ensuring rapid mitigation of threats. This is particularly important in ERP systems, where the integration of multiple modules and frequent updates can make manual threat detection and response time-consuming and error-prone.
Remember, one of the biggest benefits of ERP is customization. Well, RASP instances are equally customizable. This allows you to get the most out of your ERP system while operating with confidence. Meanwhile, your application-specific security measures ensure that even the most sophisticated attacks are detected and neutralized before they can cause harm.
Waratek vs. Other RASPs
Waratek is technically a RASP solution, but it operates differently than other RASPs in Java and ERP environments. Like other RASPs, it embeds security policies directly into an application’s runtime. This integration allows Waratek to provide real-time protection without the need for code modifications, offering a non-intrusive yet highly effective security layer. At runtime, Waratek monitors and analyzes the behavior of ERP applications continuously. Once it understands your application’s normal operation patterns, Waratek can detect anomalies and potential threats in real-time.
But Waratek is a unique solution even among other RASPs. This is primarily due to its comprehensive coverage and the depth of its monitoring capabilities. Waratek can be deployed across all your ERP modules simultaneously, with very little setup. Once active, it will run continuously and can scale and change along with your systems without requiring any downtime or changes to the code base.
Waratek can detect and block each of the threats which pose the greatest risk to ERP systems. These include SQL injection, cross-site scripting (XSS), and deserialization attacks. Each of these attack methods are primed to penetrate perimeter defenses, but rely on minimal internal security and segmentation to make it to the crown jewels.
For example, consider the MOVEit attack we mentioned above — a SQL injection attack wherein the attackers moved laterally between modules after initial access. Such an attack would not be possible for organizations running Waratek, which can intercept and analyze SQL queries at runtime. If an attacker attempts to inject malicious SQL commands to gain unauthorized access or move laterally across ERP modules, Waratek’s real-time analysis can identify the abnormal query patterns and block the attack before it can cause harm. This level of protection is far more sophisticated than traditional perimeter defenses, which may not have the visibility or context to detect such threats effectively.
Moreover, Waratek’s approach to security automation significantly reduces the workload on IT and security teams. The platform’s ability to enforce security policies dynamically minimizes the need for manual intervention. Manual security processes can be error-prone and time-consuming, but with Waratek’s automation ensures that threats are mitigated rapidly and properly.
The Future of ERP Security with RASP
The landscape of ERP systems is rapidly evolving, driven by trends such as increased cloud adoption, AI integration, and the need for enhanced cybersecurity. These advancements, while beneficial, also introduce new vulnerabilities and threat vectors that traditional security measures may struggle to address. RASP, with its ability to monitor and protect applications in real-time, provides a critical line of defense against these threats.
RASP as a technology — and Waratek in particular — is evolving to future-proof ERP security by incorporating features like advanced analytics, machine learning, and integration with other security tools to offer more comprehensive protection. These advancements will help RASP remain effective against increasingly sophisticated attacks.
As ERP systems continue to integrate new technologies and expand their capabilities, RASP will remain a cornerstone of effective cybersecurity strategies, helping businesses maintain confidence in their operational and data integrity.
To learn more about how RASP can enhance the security of your ERP systems, we encourage you to explore Waratek’s suite. For more information, please visit our Waratek RASP Solutions page or contact our team here to schedule a consultation.




