[Update June 18, 2019]
[Update June 18, 2019]
Oracle have issued a patch for this new vulnerability CVE-2019-2729
Please note that this Oracle fix has the same limitations as their previous fix.
Oracle’s patch is available only for certain support tiers.
- The Oracle patch only fixes versions 10.3.6 or 12.1.3 of WebLogic; users on older versions must upgrade to apply the security alert patch for CVE-2019-2725
- All servers must be current on the latest PSUs
[Update June 17, 2019]
Since our last update on May 22nd Palo Alto Networks Unit 42 have identified a new variant of Echobot, an offshoot of the Mirai family of Internet of Things botnet, which is targeting Remote Code Execution vulnerabilities including CVE-2019-2725. Oracle released an update for this vulnerability on 26th April, the day after their quarterly CPU, due to its seriousness.
WebLogic users are still at risk
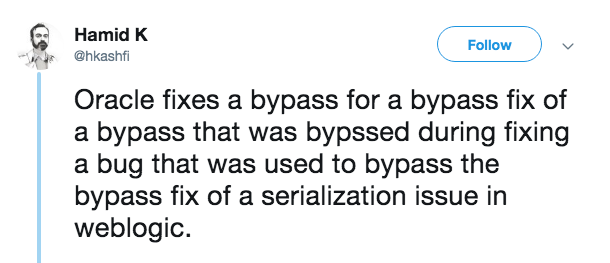
According to an update from the KnownSec 404 security team, Oracle’s fix for CVE-2019–2725 has been bypassed again. Reports on Twitter suggest that exploits which bypass Oracle’s fix have already been found in the wild.
The reason that Oracle has struggled to fix this vulnerability is that they use a blacklist mitigation strategy in WebLogic. All the attackers have to do is create alternative payloads that do not use the blacklisted gadgets (components). This is the classic whack-a-mole game. As long as Oracle keeps using a blacklist mitigation strategy, attackers and security researchers will keep bypassing Oracle’s fixes. It’s a never-ending game.
Because of Oracle’s blacklisting approach, WebLogic users are not protected against CVE-2019-2725 payload variants and deserialization zero-day exploits even if they are using the latest patches from Oracle.We think @hkashfi summarised it well here
Waratek fully remediates deserialization vulnerabilities
Waratek’s deserialization solution does not use blacklisting of gadgets and therefore it is immune against any kind of payload variants, alternative exploits, zero-days etc., and it is entry point agnostic. Therefore, once you have implemented Waratek, you are protected against deserialization vulnerabilities – full stop.
Act now
The severity of this vulnerability is critical which allows a full compromise of the server (RCE). Remote code execution vulnerabilities can be exploited by cryptomining malware, ransomware and are also used to achieve data breach and exfilration.
Read our case studies here and contact us to find out more.
[Update May 22, 2019]
Last month, we issued a security advisory to all Waratek customers regarding a critical vulnerability in Oracle’s WebLogic servers (CVE-2019-2725). Oracle issued a security alert strongly advising all customers apply the updates provided as soon as possible, listing affected version as 10.3.6.0, 12.1.3.0.
This updated communication is to advise that the Waratek research team has verified that older versions of WebLogic, not listed in the Oracle Security Alert, still contain the RCE vulnerability reported in CVE-2019-2725. We have tested and verified the presence of the vulnerability in at least 2 version previous to 10.3.6.0 and 12.1.3.0. Our remediation advice remains unchanged and WebLogic users should take steps to protect their systems. Waratek’s original remediation guidance is below for reference. Waratek customers can contact their account manager or info@waratek.com if they have any questions.
[Update April 28, 2019]
Following up on Waratek’s guidance issued on April 24, 2019, Oracle has officially confirmed the zero-day deserialization remote command execution vulnerability originally reported publicly by researchers at KnownSec 404. This critical vulnerability (CVE-2019-2725 with CVSS score of 9.8) affects all WebLogic versions (including the latest version) that have the wls9_async_response.war and wls-wsat.war components enabled.
Oracle issued a security alert on Friday, April 26, 2019 strongly advising all customers apply the updates provided by this Security Alert as soon as possible. The patch that Oracle’s Security Alert Program has made available is only provided for product versions that are covered under the Premier Support or Extended Support phases of Oracle’s Lifetime Support Policy.
Waratek advises all WebLogic users to be aware of the following points as they pertain Oracle’s available remediation for CVE-2019-2725:
- Oracle’s patch is available only for certain support tiers, please see linked Oracle policy above.
- The Oracle patch only fixes versions 10.3.6 or 12.1.3 of WebLogic; users on older versions must upgrade to apply the security alert patch for CVE-2019-2725
- All servers must be current on the latest PSUs
Immediate Action is Necessary
It has been reported that this critical vulnerability is under active exploit, we urge all WebLogic users to take steps to remediate as soon as possible. It should also be noted that a successful attack could lead to a full compromise of the WebLogic server.
Waratek’s Customers Are Already Protected
- Existing Waratek Secure and Waratek Enterprise customers who have enabled the deserial zero-day (CWE-502) rule in protect mode, are already protected. No further action is required.
- Existing Waratek Patch customers who have enabled the Process Forking ARMR rule in protection mode, are already protected.
- Waratek’s ARMR platform provides complete remediation to this zero-day critical vulnerability and therefore, Waratek customers do not have to apply Oracle’s hot fix for CVE-2019-2725 with urgency.
- Non-Waratek customers who are affected by this Oracle WebLogic vulnerability and are interested in instant protection outside of Oracle’s support parameters, as well as those using inefficient solutions based on pattern matching and signatures, should contact Waratek at info@waratek.com.
[Original Guidance, posted April 24, 2019]
We’ve been alerted to a potential WebLogic zero-day from a credible source. According to the reports, Oracle WebLogic wls9_async and wls-wsat components trigger a deserialization remote command execution vulnerability. This vulnerability affects all WebLogic versions (including the latest version) that have the wls9_async_response.war and wls-wsat.war components enabled.
At this point the vulnerability has not been fixed by the supplier.
Waratek Customer Advice
- Existing Waratek Secure and Waratek Enterprise customers who have enabled the deserial zero-day (CWE-502) rule in protect mode, are already protected against this new zero-day. No further action is required.
- Existing Waratek Patch customers who have enabled the Process Forking ARMR rule in protection mode, are already protected against this new zero-day.
Non-Waratek customers who are affected by this new Oracle WebLogic 0-day and are interested in instant protection without depending on the vendor’s patch availability, as well as those using inefficient solutions based on pattern matching and signatures, should contact Waratek at info@waratek.com.
About Waratek
Waratek is an award-winning pioneer in the next generation of application security solutions. Using patented runtime protection technology, Waratek makes it easy for teams to secure business critical applications and securely extend the life of their legacy applications. We provide some of the world’s largest brands with:
- Instant patching of known software flaws with Runtime Virtual Patches
- Protecting applications from known and unknown attack vectors such as the OWASP Top Ten and SANS Top 25
- Virtually upgrading out-of-support Java applications and platforms to the most current version without rewriting the app