The quarterly Oracle Critical Patch Update (CPU) for January 2022 is available and, if December wasn’t a good enough indicator with the Log4j vulnerabilities, the industry is experiencing a 3-year high by hitting a staggering 497 patches, continuing the upward trend line of vulnerabilities over the last three years.
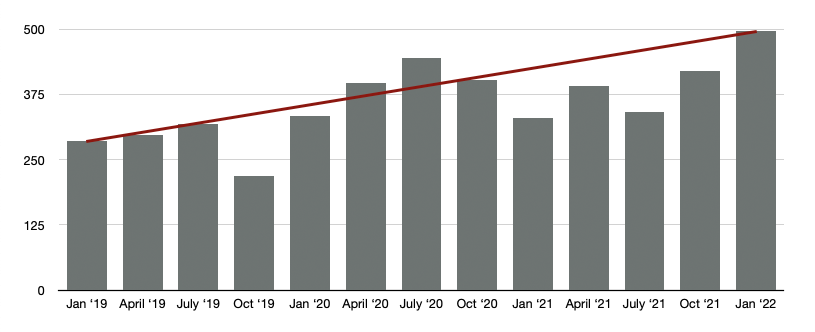
The increase of CVEs suggests that there are 5.5 new CVEs per day. If you go to bed having patched your application to 100%, by the time you wake up, get to the office, and have your morning coffee, you’re already 2 CVEs behind. In the current security climate when you’re not actively taking a step forward, you’re taking a step back.
Given the upward trend of vulnerabilities and the increase in severity, what can you do to protect yourself?
The Paradox of Progress
The best way to address the vulnerabilities to apply the Critical Patch Update as soon as possible. However as I explained above, due to the sheer volume and rate at which new vulnerabilities come out, that may not even be enough.

The moment the CPU is released, hackers begin reverse engineering the binaries as seen in the example above from October 2020. Once they have bypassed the fixes, they often receive rewarding feedback such as:

Look, my intent here is not to criticize the efficacy of, nor the effort that goes into the CPU. Applying the patches is an important action, but there’s only two sure fire ways to increase your security posture and truly prevent exploits:
- Dedicate sufficient human capital to fix the vulnerable code
- Leverage a security platform that autonomously fixes the vulnerable code in memory
Both of these options are valid solutions, however, only one of them has a predictable investment. Hiring a team of people to constantly review and test code in real-time, patch the new CVE that comes out every several hours, just isn’t feasible.The effort and cost alone would be uncontrollable and unscalable. Leveraging an autonomous solution is not only scalable, but the investment is affordable and predictable.
Decreasing Your Security Risk Profile
You may be thinking to yourself, “Yeah, I get it, I can only solve this if I spend money on another security solution. Shocker.” You may even already use a typical solution that scans code for vulnerabilities that it’s aware of. However, being aware of the vulnerabilities is only one-half of the way towards a solution.
WAFs may seem like a logical step for securing your applications, but it’s important to remember that they’re not a failsafe solution. WAFs are fraught with problems like:
- Generation of false positive and false negatives
- Lack protection against Zero-Day exploits
Perhaps the most important limitation is the fact that they can be easily bypassed. And when I say “easy,” I mean that by the next day after Log4j was in the news, Twitter was already crawling with bypasses, as seen below.

If WAFs are a step in the right direction, how are we supposed to reliably and scalably strengthen our security posture? To answer that, I present you with an analogy.
If you are allergic to nuts and you are eating at a restaurant, you’re going to scan the menu for any items that contain nuts. You are going to ask the waiter and you’re going to look at your meal when it comes out to see if you can see any nuts in the dish. That’s how the typical solutions work, by scanning, looking for the nuts that they know should not be there.
Now imagine a solution that sits in the kitchen and autonomously removes the nuts from the dish as the chef puts them in. That’s the power of autonomous security at the application runtime.
If that’s how you’re looking to confidently decrease your Security Risk Profile without dedicating internal resources to divert focus to handling the never-ending technical debt, there’s one place to look: Waratek ARMR,
Only Waratek provides a fully programmable security platform, ARMR, that can autonomously remediate vulnerabilities inside the binary code. Unlike other security products that just attempt to block known exploit payloads, Waratek actually remediates the vulnerable code inside an application’s executing code in real-time and with no interruption to service or degradation of performance.
Some of the world’s leading companies use Waratek’s ARMR Security Platform to patch, secure and upgrade their mission critical applications. A pioneer in the next generation of application security solutions, Waratek makes it easy for security teams to instantly detect and remediate known vulnerabilities with no downtime, protect their applications from known and Zero Day attacks, and virtually upgrade out-of-support Java applications – all without time consuming and expensive source code changes or unacceptable performance overhead.
For more information on how Waratek can help your organization, contact us.
