In late July, Amy DeMartine of Forrester made a bold prediction:
“…eventually runtime application self-protection (RASP) (will) take over web application firewall (WAF) as the best way to combat web app attacks. They have deeper knowledge than WAFs of the applications that they protect, and they can virtually patch vulnerabilities and weaknesses. In an upcoming report, we’re predicting WAF market growth to significantly slow down over the 2021–2023 period as bot management and RASP tools fully cover traditional WAF capabilities. In fact, RASP will experience a healthy 26.2% CAGR in the same period.”
Longstanding frustrations with WAF coupled with high profile security events and new regulations like GDPR are driving the push to newer technologies like runtime protections. For years, WAF have frustrated security teams with their high false positives and performance killing overhead. Spend enough time with a WAF engineer and they’ll tell you about all the time spent running in monitor mode or with just enough rules applied to pass an audit.
It is somewhat ironic that the same regulatory environment that helped create demand for WAF is also driving companies to newer, more effective alternatives. PCI compliance drove the vast majority of WAF installations. Now GDPR and it’s “security by design/protection by default” criteria is driving organizations to look at protections that can address basic security more effectively and tackle related issues like patching and legacy software upgrades that WAF cannot fix.
WAF vs RASP
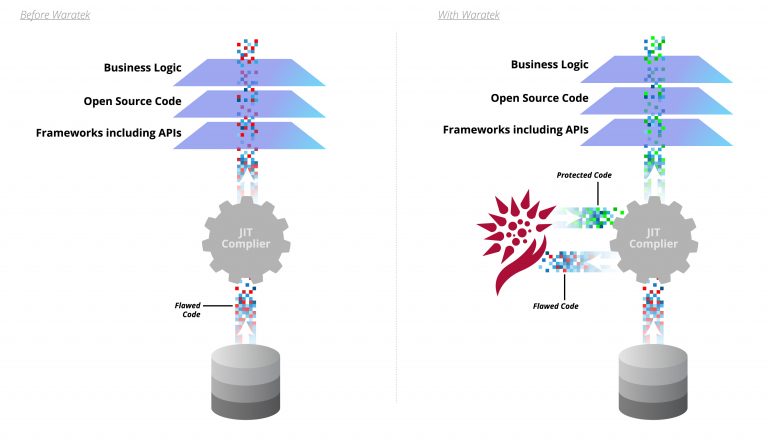
For example, take a look at how Waratek’s runtime protection using proven compiler techniques compares to WAF and the advantages of Waratek’s approach become clear.
|
WAF Technology |
Waratek / Runtime Protection |
|
|
No profiling or routine tuning |
✘ |
✔︎ |
|
No instrumentation/filters (heuristics) |
✘ |
✔︎ |
|
No false positives – guaranteed |
✘ |
✔︎ |
|
Run in blocking mode with low/no performance hit |
✘ |
✔︎ |
|
Remediate CVEs with no downtime or source code changes |
✘ |
✔︎ |
|
Virtual upgrade of out of support Java applications |
✘ |
✔︎ |
WAF may still find a home in organizations that are dedicated to a defense-in-depth strategy. Over the long term, though, compiler based runtime solutions offer the best protection against the increasingly complex and frequent attacks against known CVEs – without the side effects or time and resources required by WAF.